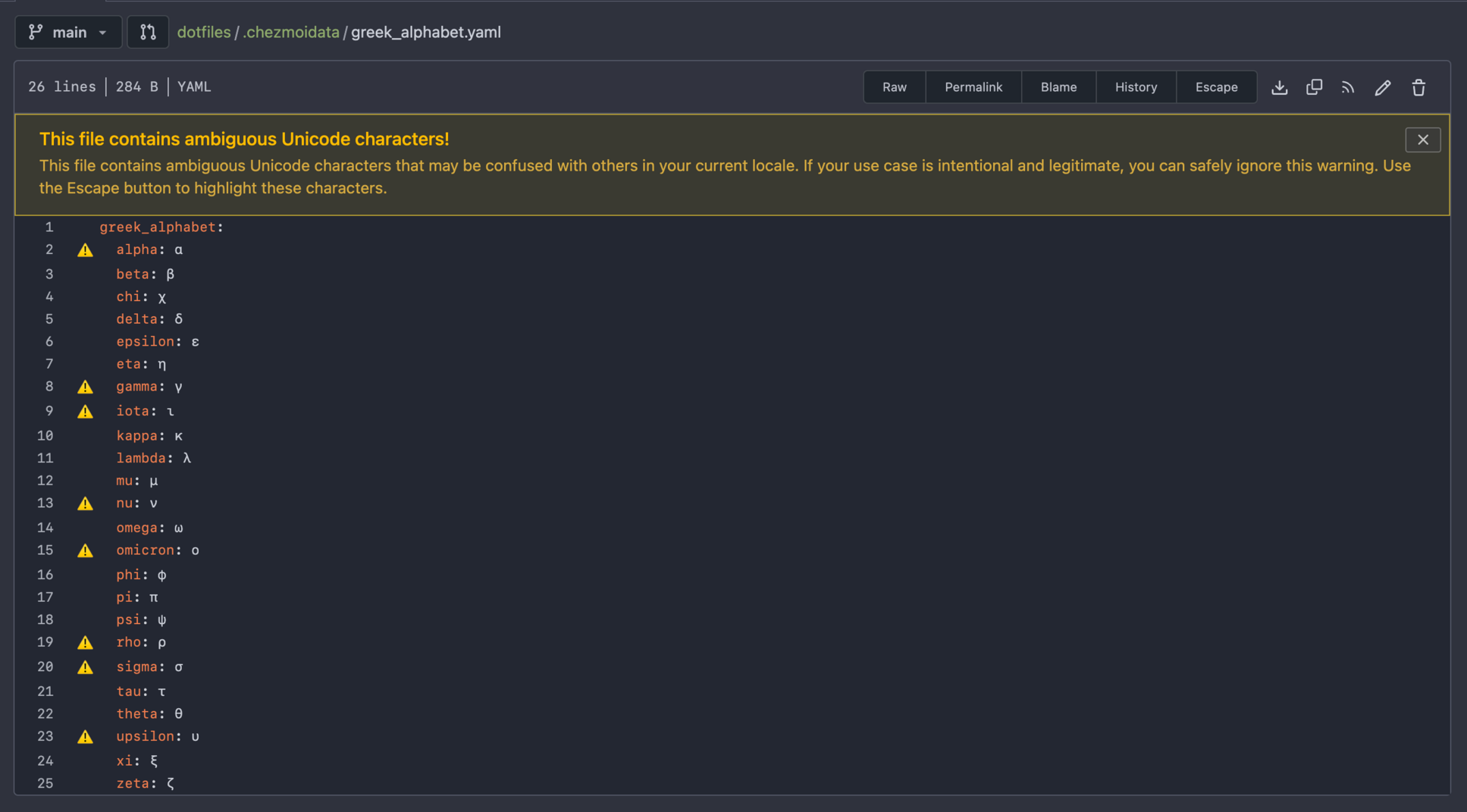
Interesting which characters Gitea labels as “ambiguous.”
This concert video on an HDR screen is both impressive and blinding.
“The much-beloved BookTok sensation…”
Hmm. No thank you, book synopsis writer, I think I will skip this one.
Perhaps the most bizarre experiment was conducted in Paris, in April 1746, by Jean-Antoine Nollet. Using a snaking line of some 200 monks connected by a mile-long iron wire, Nollet observed their reactions when he administered a powerful electric current through the wire. The simultaneous screams of the monks demonstrated that, as far as Nollet could tell, voltage was transmitted through a conductor “instantaneously.”
I’m going to miss Reddit. It’s been an irregular part of my life for 12 years now. It’s been responsible for countless rabbit holes and ideas, discussions and explorations. Rest in peace, 2010’s era of the internet.
Made a simple command-line Swift script:
> dict quasar
quasar qua·sar | ˈkwāˌzär | noun […]
> dict -o quasar
Opening Dictionary.app…
It was just another day doing errands, traveling the same three or four routes that made up 90 percent of life. Looking for seeds to eat. This is normal, the bird thought, the only thing it ever thought.
Fell for this one. I would listen, I think. Costerton drops rap album to attract Gen Z to ICANN
I have been waiting for .foo! Google to drop EIGHT new gTLDs
Interesting look at the DNSSEC signing ceremony Verisign’s Role in Securing the DNS Through Key Signing Ceremonies
The registrar behind .tm, .sh, .io, & .ac (Divido) just released a flurry of single-character domain names on .tm for $30,000 a piece. Think a.tm.
Far too pricey for an individual and it’s risky to put a business on another country’s ccTLD. But who am I to throw stones? I still use zacwe.st for my website.
Anyway, pipe dream: z.ac would be a fun one. Only $80,000!
Why yes, I am backing up my NAS right now, how did you know?
This peep has lived a very hard life.

DevUtils.app, besides being incredibly useful, also injects a fun little whimsy in its random string generator. Ocean string!
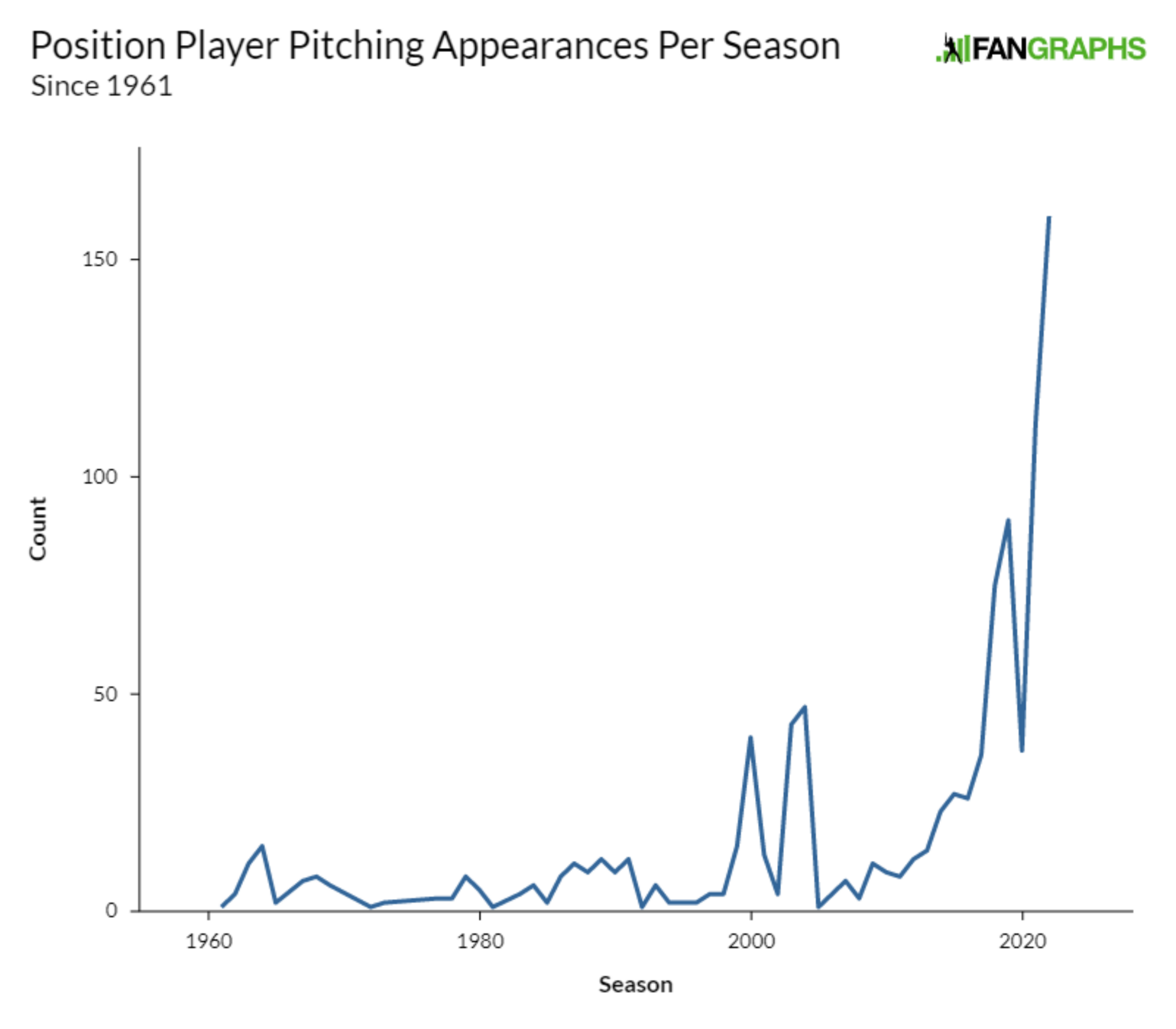
Interesting seeing the rate of position players pitching over time. Look at that hickey stick growth! Almost a non-event now.
From Stop Wasting Everyone’s Time and Quit Already
The San Francisco Public Library app is pretty good for both physical books and ebooks. It’s able to check out an ebook and send it to Kindle without another app.
Wrote a blog post about using Uptime Kuma’s “push” monitors to track e.g. cron jobs.
Using Uptime Kuma push monitors
Uptime Kuma has a “push” monitor type which supports sending in status updates for something like a cron job to make sure it continues to execute. I use this for tasks like running backups or cleanup chores.
Aside: To avoid tying monitoring to my normal infrastructure, I’ve been successfully running Uptime Kuma on fly.io. I also recommend Cronitor for a similar commercial offering but its pricing doesn’t align well with my personal projects.
Normally to update Uptime Kuma you might append && curl … to invoke the monitor URL at the end of a script. I think this is a little too limiting, so I’ve written a small script that wraps an underlying command with a monitor update:
#!/bin/bash
if [ $# -lt 1 ]; then
echo "Usage: $0 <push_token> [command...]" >&2
exit 1
fi
push_token=$1; shift
start_time=$(date -u +%s%3N)
if [ $# -gt 0 ]; then
"$@" || exit
fi
end_time=$(date -u +%s%3N)
duration=$(($end_time - $start_time))
result=$(curl --fail --no-progress-meter --retry 3 "https://uptimekuma.example.com/api/push/$push_token?ping=$duration" 2>&1)
if [ $? -ne 0 ]; then
echo "Failed: $result" >&2
fi
This script is invoked with the token and an optional underlying command to execute and report to Uptime Kuma when the command is successful along with its execution time as the ping property. For example:
kuma 3EpwDA93fC docker system prune -a -f
I’ve automated this using the ansible-uptime-kuma Ansible collection to automatically create “push” monitors for recurring jobs and “http” monitors for web-facing services. This ends up looking something like the following for a push monitor:
- name: Store the monitor name
set_fact:
monitor_name: "{{ inventory_hostname }}-borgmatic"
- name: Create Uptime Kuma push monitor
delegate_to: 127.0.0.1
lucasheld.uptime_kuma.monitor:
api_url: "https://uptimekuma.example.com"
api_token: "{{ uptime_kuma_api_token }}"
type: push
name: "{{ monitor_name }}"
interval: 3600
- name: Get Uptime Kuma push monitor info
delegate_to: 127.0.0.1
lucasheld.uptime_kuma.monitor_info:
api_url: "https://uptimekuma.example.com"
api_token: "{{ uptime_kuma_api_token }}"
name: "{{ monitor_name }}"
register: monitor_info
- name: Set Uptime Kuma push token
set_fact:
push_token: "{{ monitor_info.monitors[0].pushToken }}"
- name: Create borg cronjob
cron:
name: "Borg backups"
job: "/usr/local/bin/kuma {{ push_token }} /usr/local/bin/borgmatic create"
minute: 33
This creates a monitor for my borgmatic cron and executes it hourly. When it fails to check in, Uptime Kuma sends me notifications, and when it succeeds it keeps track of how long it takes to execute. Perfect!
I track my reading in Calibre and export it to my website to disseminate. Just made my by-rating and by-author pages use sections. For example, all of the books by Jim Butcher that I’ve read. Significantly easier to link people to recommendations now.
Received my first Year of Sanderson box today, pleasantly surprised by the contents. I also enjoyed seeing my neighbors receive theirs in the mail room.